The default host name of WSO2 Carbon based products is "localhost" which can be configured through "HostName" property in CARBON_HOME/repository/conf/carbon.xml. If this value is "localhost" the management console url looks like https://lcoalhost:9443/carbon/ (You can observe this value at server startup).
[Unknown]: wso2.com
Now if you try to login with openid url, the login will be successful.
But most of the time, it's preferred to use some other suggestive value for host name rather than using default value.
e.g. wso2.com so that managment console url will look like https://wso2.com:9443/carbon/
In this blog post I'm going to use WSO2 Identity server as the Carbon based product since by default WSO2 IS supports SSO via OpenID. But same steps are applicable to all other WSO2 products.
In order to change the host name and management console url, you have to change the host name value in CARBON_HOME/repository/conf/carbon.xml to wso2.com as I've done below.
Change identity.xml as follows.
If you are a Ubuntu user, then you have to add following entry in /etc/hosts file
127.0.0.1 wso2.com
If you are a windows user, then above file is located at c:\windows\system32\drivers\etc\hosts
Now if you start the server, you'll see that it starts without any errors. After the server successfully starts, sign in as admin user and go to My Identitys -> InfoCard/OpenID and copy the OpenID url provided by WSO2 Identity Server which will look like "https://wso2.com:9443/openid/admin"
If you use this url to sign in to an external SSO client or internal client provided by WSO2 IS, you'll encounter following error.
[2012-03-30 10:37:52,427] ERROR {org.wso2.carbon.identity.relyingparty.ui.openid.OpenIDConsumer} - 0x704: I/O transport error: hostname in certificate didn't match: !=
org.openid4java.discovery.yadis.YadisException: 0x704: I/O transport error: hostname in certificate didn't match: !=
To overcome this, relevant certificate should be imported to keystore used by WSO2 IS or you can specify a new keystore which has a matching public certificate.
The steps needed to create a keystore with matching certificate and configure IS to use that keystore can be found in this blog post written by Hasini.
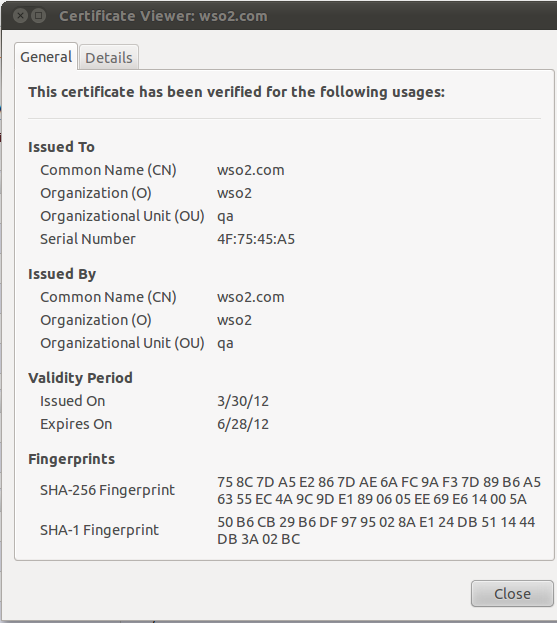
In creating the new keystore, you should keep in mind to provide the host name of your new carbon server as the Common Name (CN).
e.g. :
keytool -genkey -alias iscert -keyalg RSA -keysize 1024 -keypass password -keystore iskeystore.jks -storepass password
What is your first and last name?
What is the name of your organizational unit?
[Unknown]: qa
What is the name of your organization?
[Unknown]: wso2
What is the name of your City or Locality?
[Unknown]: Colombo
What is the name of your State or Province?
[Unknown]: Western
What is the two-letter country code for this unit?
[Unknown]: SL
Is CN=wso2.com, OU=qa, O=wso2, L=Colombo, ST=Western, C=SL correct?
[no]: yes
After you successful configure IS to use new key store start the server and access management console. You can verify your configuration by viewing the browser certificate.

Now if you try to login with openid url, the login will be successful.
